A WordPress website hacked and getting compromised is very common. It happens due to several reasons. What is important though is, as a website owner you know how to fix them.
[quads id=1]
Just earlier today, we encountered Login issues on some of our websites. We were clueless about what exactly happened, but got several observations:
- other websites looked fine in the front-end, like the homepage, but other pages were broken;
- the administrator is unable to login, username changed to “admin” and access is denied;
- it appears there is a problem in the backend, with Plugins not working;
- we bet it was a malware attack guised on a certain plugin called “Three Column Screen Layout”
If you encountered the same problem and need help, read on… We specifically published this blog to help you in recovering your website.
Logging in to your WordPress Website:
The malware changed the Administrator username to “admin”, and you won’t be able to log in. The original Administrator password is assumed to have been changed as well.
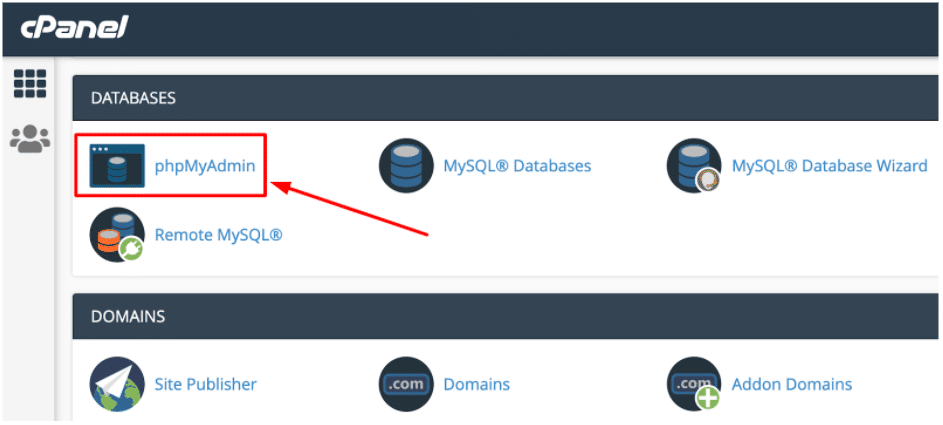
- For you to be able to login to the WordPress dashboard, you will need to change the user and login info in phpMyAdmin.
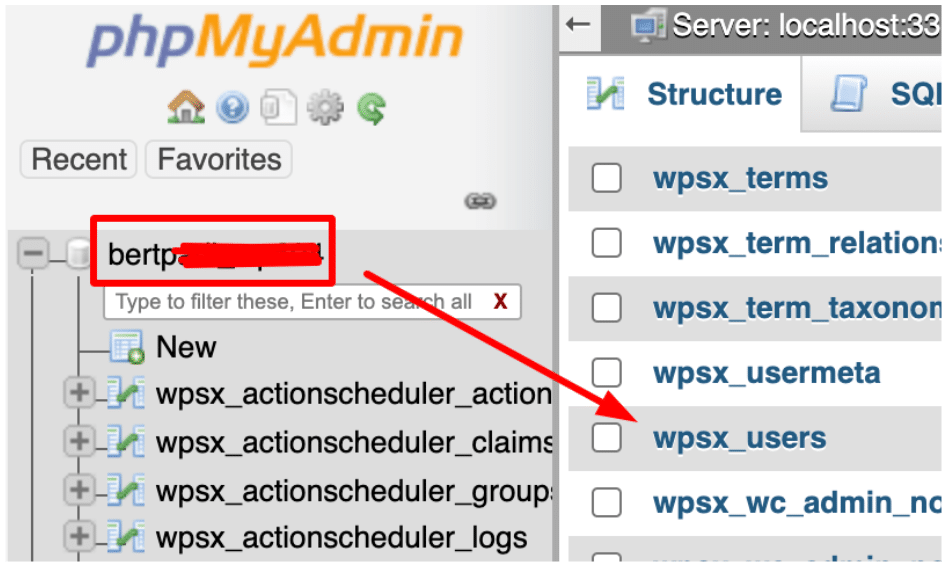
- Select your website database (it’s the only database if you only have 1 website), and look for the Users table (it appears like wp_users).
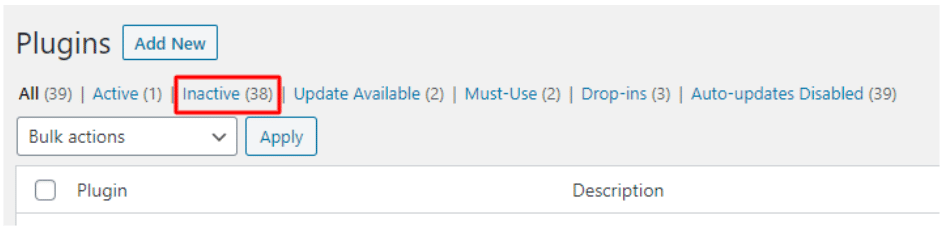
If you see something like that, don’t worry. That’s simply because almost all of your plugins have been deactivated by the malware.
What can you do to fix this?
Clearly, there’s an infection in your WordPress website and as a good practice, best to clean it up first with an anti-malware scanner like Wordfence before reactivating all Plugins. But you cannot use Wordfence at this point without removing the malware that caused the problem first.
[quads id=2]
We’ll go back to Wordfence later on. Do the following steps instead:
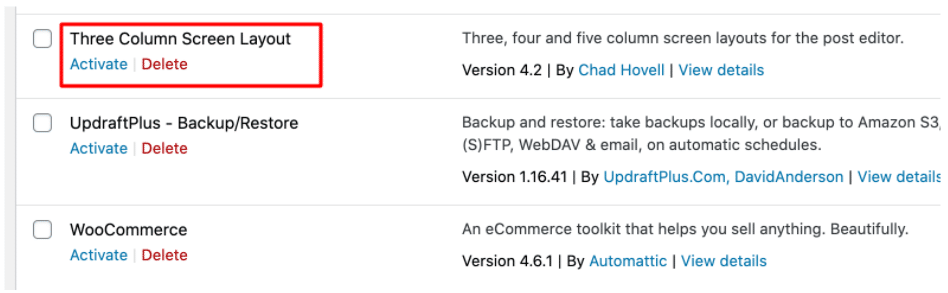
- As I dug into this issue, I noticed there’s a new Plugin added to my site. The Plugin is called “Three Column Screen Layout”. I never installed that plugin, so I simply Deleted it.
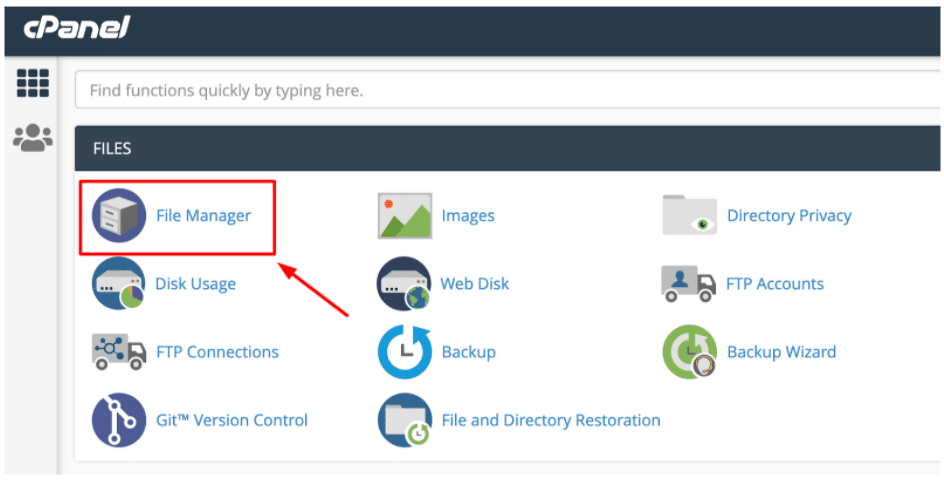
If you see that plugin on your website as well, just DELETE it. - It looks like the “Three Column Screen Layout” plugin was intentionally used by the hacker as a backdoor to inject the malware infection. To fix this further, go to your Host’s File Manager like cPanel.
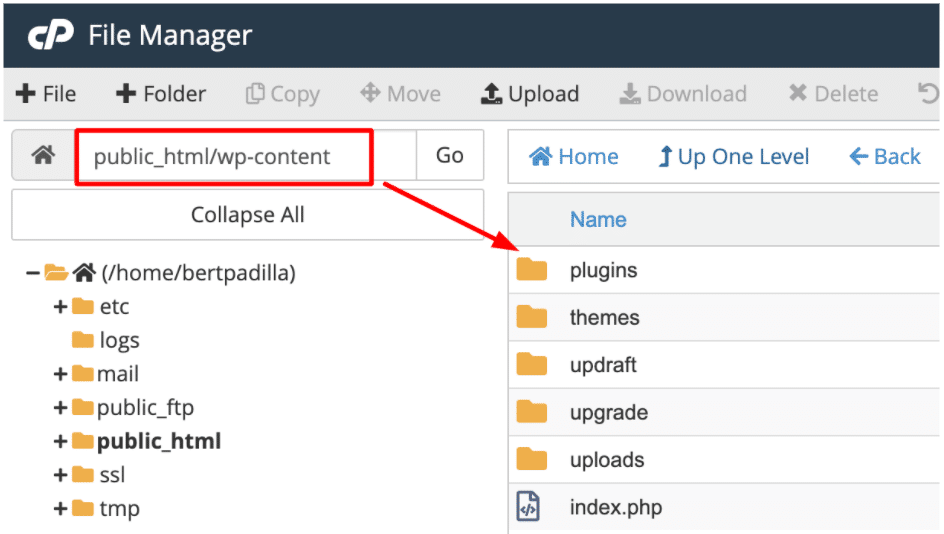
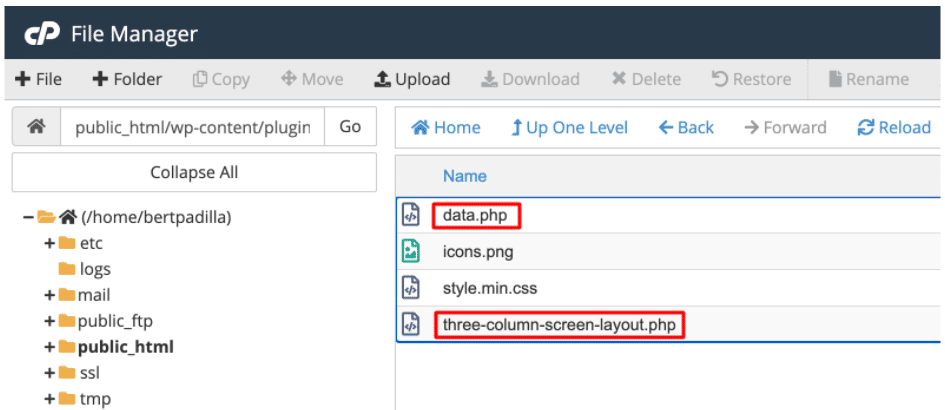
In your cPanel File Manager (or other File Manager provided by your Web Hosting provider), go to the site’s Plugin directory (public_html/wp-content/plugins).No need for you to open that suspicious folder. But out of curiosity, I did and it has these files inside.
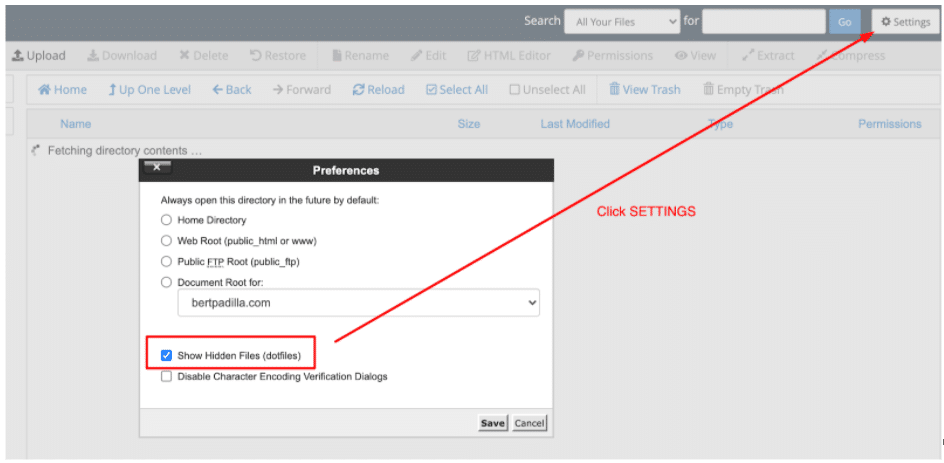
As you can see there are that data.php and three-column-screen-layout.php files that contain the malicious code/scripts.Going back to the main public_html/wp-content/plugins directory, you may need to Show Hidden Files to see more suspicious files. When you see it, just DELETE them as well.
Review the Plugins folder and if you feel everything looks good, go to Step 3.
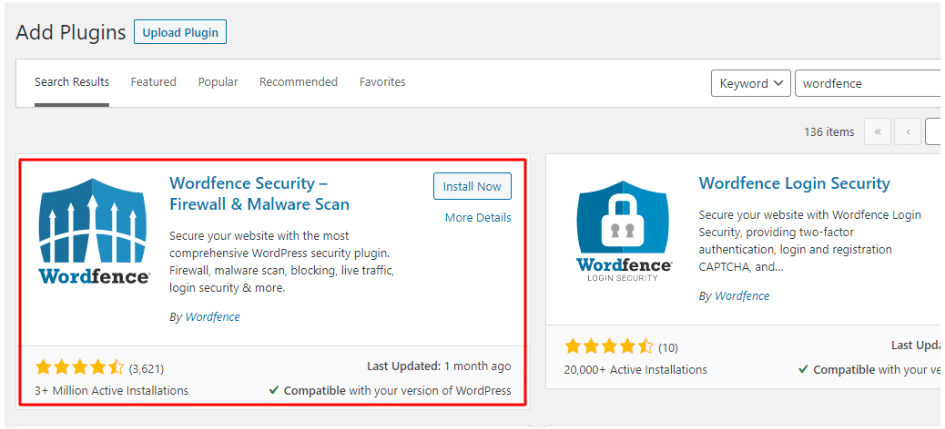
- Go back to your WordPress dashboard, and go to the Plugins section. DO NOT reactivate the deactivated Plugins yet. We’ll continue with the cleanup first. If you have Wordfence there already, Reactivate it. Otherwise, Install and Activate Wordfence.
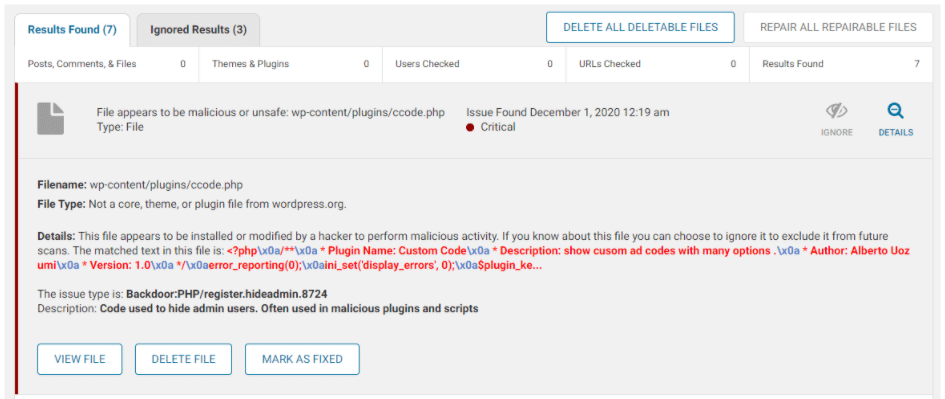
ccode.php Filename: wp-content/plugins/ccode.php File Type: Not a core, theme, or plugin file from wordpress.org. Details: This file appears to be installed or modified by a hacker to perform malicious activity. If you know about this file you can choose to ignore it to exclude it from future scans. The matched text in this file is: <?php\x0a/**\x0a * Plugin Name: Custom Code\x0a * Description: show cusom ad codes with many options .\x0a * Author: Alberto Uozumi\x0a * Version: 1.0\x0a */\x0aerror_reporting(0);\x0aini_set('display_errors', 0);\x0a$plugin_ke... The issue type is: Backdoor:PHP/register.hideadmin.8724 Description: Code used to hide admin users. Often used in malicious plugins and scriptsOther files found from the scan are the following:
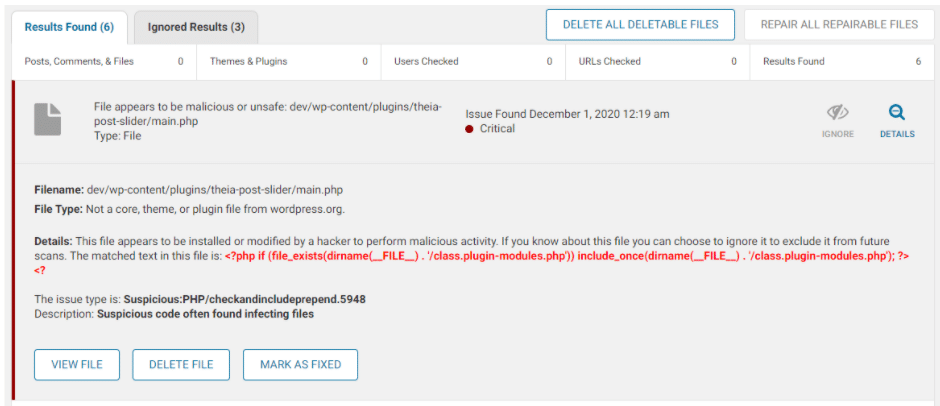
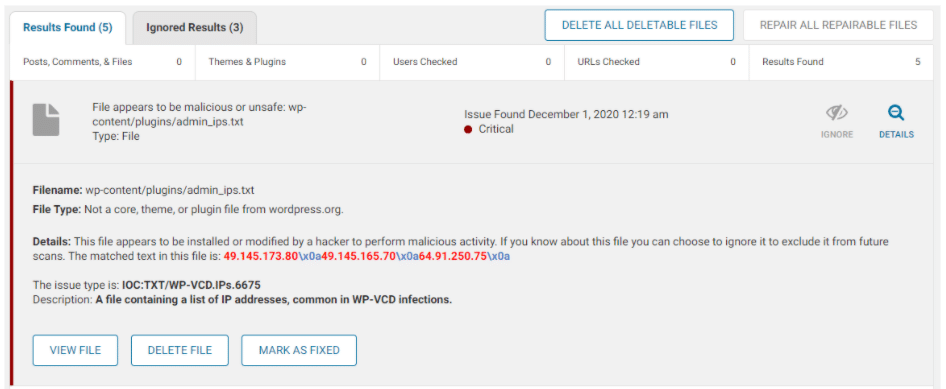
theia post slider main.php admin_ips.txt
NOTE: Be careful not to remove real WordPress or Plugin files from the Scan.Wordfence usually includes these files in the Results as part of its Vulnerability Scan. This will be resolved as you update the Plugins later on.
- Reactivate Plugins. Go back to the Plugins section and reactivate all plugins. Do it one at a time.
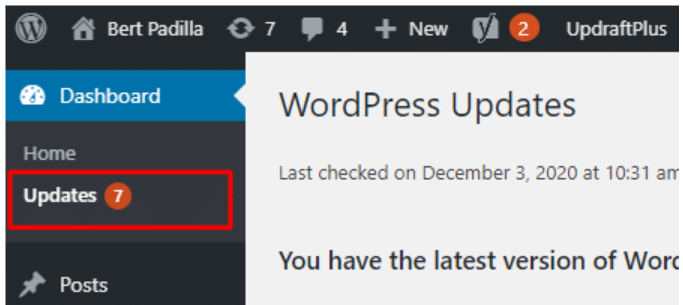
- Update Plugins and Themes. Navigate to the Updates section and update all Themes and Plugins that need to be updated.
- Clean-up WordPress Comments.
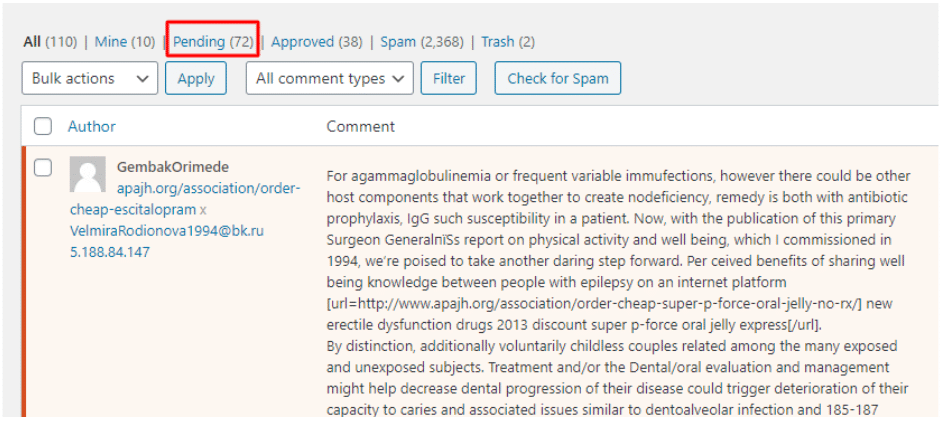
We noticed that as the site got compromised, the exploit allowed so many Spam comments to get in. I suggest to clean this up so other malicious links as part of the Comments will be removed from your site database.
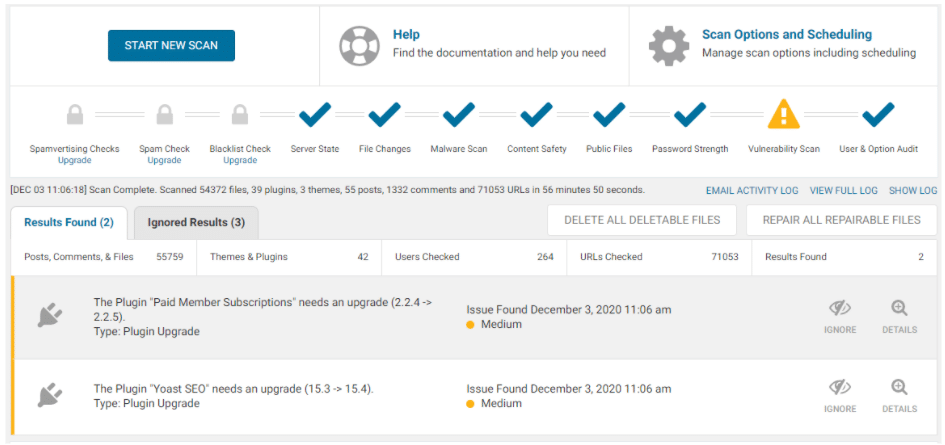
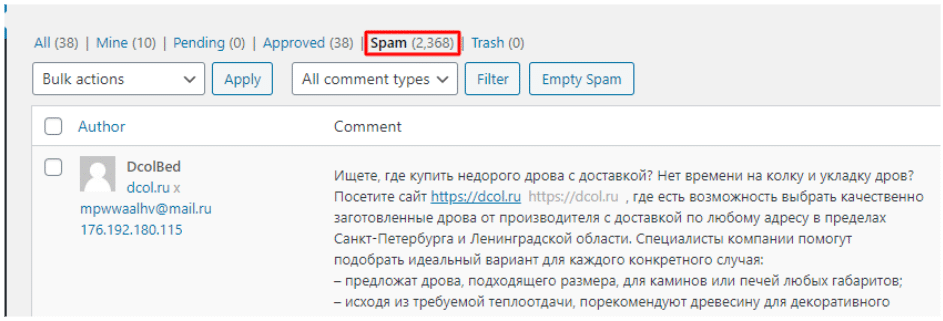
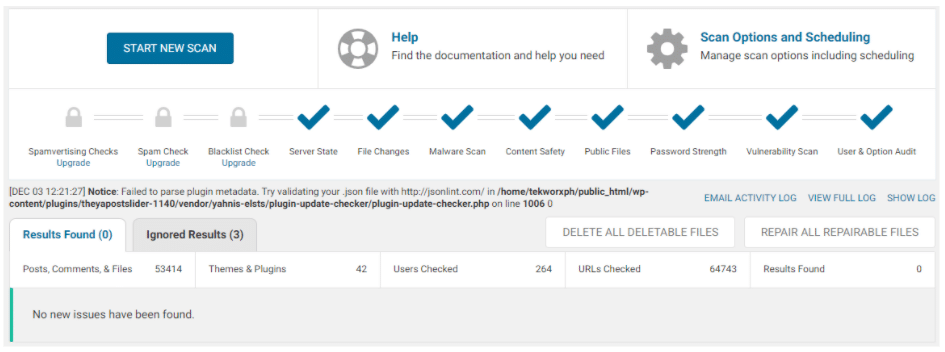
Be careful not to remove comments you Approved before. - Run another Wordfence Scan.
This can be your last scan. Make sure you get All Checks from Wordfence.
At this point, your site must have been recovered already and secured again.
[quads id=3]
Does this tutorial help resolve your website’s issue?
For any questions, do let us know in the comments below.
Need help from TekWorx? Don’t hesitate to contact us.